The Significance of a Multi-Layered Defense Approach in Cybersecurity
In the current state of technology, cybersecurity has become a crucial and never-ending fight against a constantly evolving range of malicious cyber threats. According to the 2023 Verizon Data Breach Investigations Report (DBIR) "74% of all breaches include the human element, with people being involved either via Error, Privilege Misuse, Use of stolen credentials or Social Engineering" and the "The three primary ways in which attackers access an organization are stolen credentials, phishing and exploitation of vulnerabilities." Protecting our valuable assets and data from cybercriminals is of utmost importance, and we must remain vigilant to stay one step ahead of these threats. Hackers and malicious entities are constantly finding new ways to exploit vulnerabilities, making it crucial for organizations to fortify their defenses. One of the key takeaways from the DBIR this year is that hackers are financially motivated and organized and can use many ways to attack organizations. Even though the technology being employed to fight cybercrime is getting better and better, that alone is not enough. One highly effective strategy that Cyber Op Source employs is the use of a multi-layered defense approach. This comprehensive strategy places barriers at multiple points to prevent and mitigate potential cyber threats.
Understanding the Multi-Layered Defense Approach

Source: Michael Fisher - https://twitter.com/Fisher85M/status/1030976170181976064/photo/1
A multi-layered defense approach, often called defense in depth, involves deploying a series of security mechanisms at various levels within an IT infrastructure. These layers collectively work as a cohesive unit, creating a formidable barrier against cyber threats. Each layer is designed to provide specific types of security, resulting in a comprehensive and robust defense system.
The Strength of Diversity
Mitigating Diverse Threats:
As was mention above, different layers focus on different types of security that can be applied to protect an organization. A combination of these layers can be used to fight specific types of attacks. For example, the risk associated with malware attacks can be lessened if organizations have the correct policies in place and use a combination of different types of security like perimeter security, network security, application security, and data security, to name a few. If the focus is unauthorized access, organizations should think of different layers of security that can be used to prevent unauthorized access to, for example, "data" within their organization. Policies and procedures should be written to get the job done, and different approaches, such as less privilege should be employed. This diversified approach ensures that a wide spectrum of threats is effectively mitigated.
Complicating Intruders' Efforts:
The Co-Founder David Suchomel of Cyber Op Source, often reminds the team it is not "if" but "when", when referring to cyber attacks. The statement is used to remind individuals that a cyber attack is imminent. Even though that is the case, a varied defense approach makes it more challenging for potential hackers to compromise a system. At the same time, a defensive approach should not be so stringent that it becomes impossible for employees to be productive. We must complicate an attacker's life, not valid users. A balanced approach is necessary so that even if one layer is compromised, others remain intact, impeding the progress of the attacker, not a valid user.
Adaptability and Resilience:
As cyber threats evolve, having multiple layers allows for rapid adaptation and reinforcement. In addition, new security measures can be added to address emerging threats without disrupting the existing defense structure. This approach allows for a cybersecurity system to be adaptable. A cybersecurity system should also be resilient enough to thwart off attacks. For example, let's say a CISO or ISO of an organization becomes aware of a new type of malware attack and brings it to the attention of his cybersecurity, who then checks their firewalls and antivirus solutions to make sure the organization is protected. Using this same example, let's say the cyber security team finds out that the malware successfully breached the firewall but was stopped by the IDS or other endpoint protection. That example tested the adaptability and resilience of this organization.
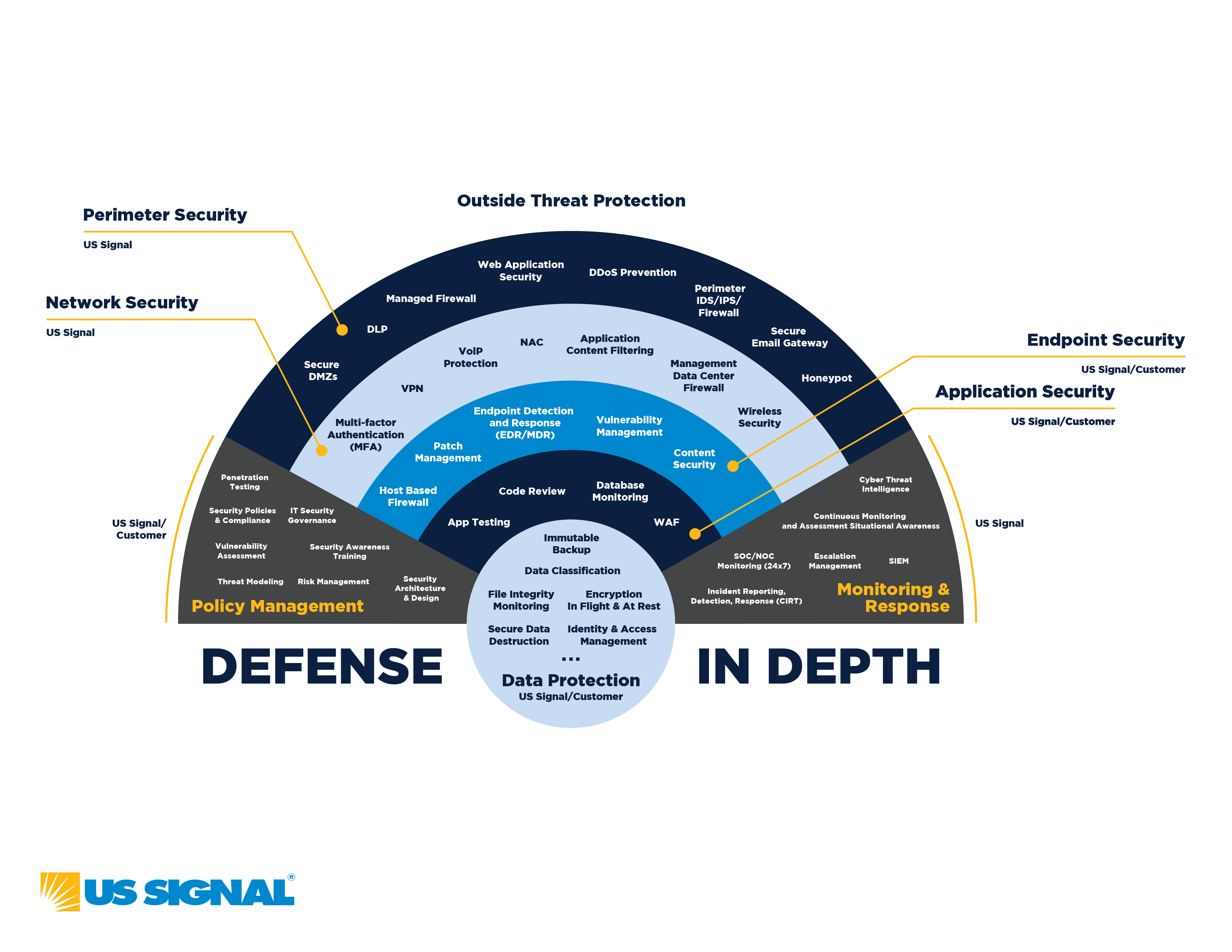
Layers of Defense: Fortifying the Digital Perimeter
Perimeter Security:
The outermost layer includes firewalls, intrusion detection systems, and intrusion prevention systems. It acts as the first line of defense, filtering incoming and outgoing traffic and preventing unauthorized access.
Network Security:
This layer focuses on securing internal network traffic. Measures like VLAN segmentation, network segmentation, and encryption ensure that even if the perimeter is breached, the attacker's lateral movement is limited.
Endpoint Security:
Protecting individual devices such as computers, laptops, and mobile devices. Endpoint security measures include antivirus software, intrusion detection, and application control.
Application Security:
It involves securing applications and software against vulnerabilities and threats. This is achieved through regular security testing, code reviews, and patch management.
Data Security:
Ensuring the security and privacy of sensitive data through encryption, access controls, and data loss prevention mechanisms. This layer focuses on protecting the core assets of an organization.
Prevention & Policy Management:
This layer acts as the governing force, defining the rules, procedures, and best practices that guide how each layer operates and interacts within the cybersecurity framework.
Operations, Monitoring & Response:
This layer involves access control management, incident response planning and execution, regular audits, employee training, monitoring of security systems, and compliance checks.
A multi-layered defense approach is fundamental to modern cybersecurity and is employed by many organizations. Cyber Op Source ensures a comprehensive defense against an evolving threat landscape by implementing diverse security measures across different levels. Through various perimeter, network, endpoint, application, and data security layers, we strive to provide our clients with a robust and resilient defense system that offers peace of mind in an increasingly digital world.
Additional References:
Takeaways from the 2023 Verizon DBIR: 9 Ways Hackers Can Use Files to Attack Your Organization